Disclosure: The views and opinions expressed right here belong solely to the creator and don’t signify the views and opinions of crypto.information’ editorial.
Because the scandal continues to unfold and specialists look at simply how severely prime officers have compromised US nationwide safety in that Sign chat leak—and embarrassed themselves by means of controversial post-statements—I wish to take a more in-depth take a look at one specific episode from the story.
You may also like: As AI rewrites historical past, blockchain know-how is a line of protection | Opinion
At first, the White Home denied that the chat ever existed. However when it turned clear that there was an excessive amount of proof to refute, they shifted ways, denying that the chat ever contained any labeled info of nationwide safety significance. And certainly, what proof can journalist Jeffrey Goldberg current after leaving that chat? Furthermore, the chat was set to self-destruct messages after a time period. So think about a courtroom listening to the place events are required to current proof, and the one out there proof consists of screenshots—in different phrases, just about nothing, as such proof is nearly inconceivable to confirm.
The reply is somewhat easy—if the journalist had taken care to correctly protect such proof. He may show that he had entry to delicate info at a time when he mustn’t have, by publishing cryptographic hash sums of that info. Had he not been within the chat, he wouldn’t have identified when and the place they have been planning to strike Yemen, who the goal was, and so forth. Sure particulars might turn into public later, however not on the time the chat occurred—right?
The answer lies in a cryptographic technique referred to as proof of existence with out disclosure. It entails two primary parts: cryptographic hashes and dependable timestamps. This may be carried out on blockchain manually—if one is aware of the method—or by means of quite a lot of functions and providers providing blockchain-based timestamping proofs.
Right here’s the way it works: you write a message (for instance, by copying and pasting from the chat), generate a hash sum of the message, publish it on a blockchain, and save the personal key for the deal with used to publish it. You’ll later want this personal key to show that it was your deal with (i.e., you personally) that revealed the hash, and thus that you simply had data of the unique message at the moment. A social media account may additionally serve an identical operate, however keep in mind that social platforms are centralised techniques—susceptible and, not like blockchains, not immutable.
So, there it’s—a notice for all journalists who might at some point have to show the existence of a truth with out revealing its contents.
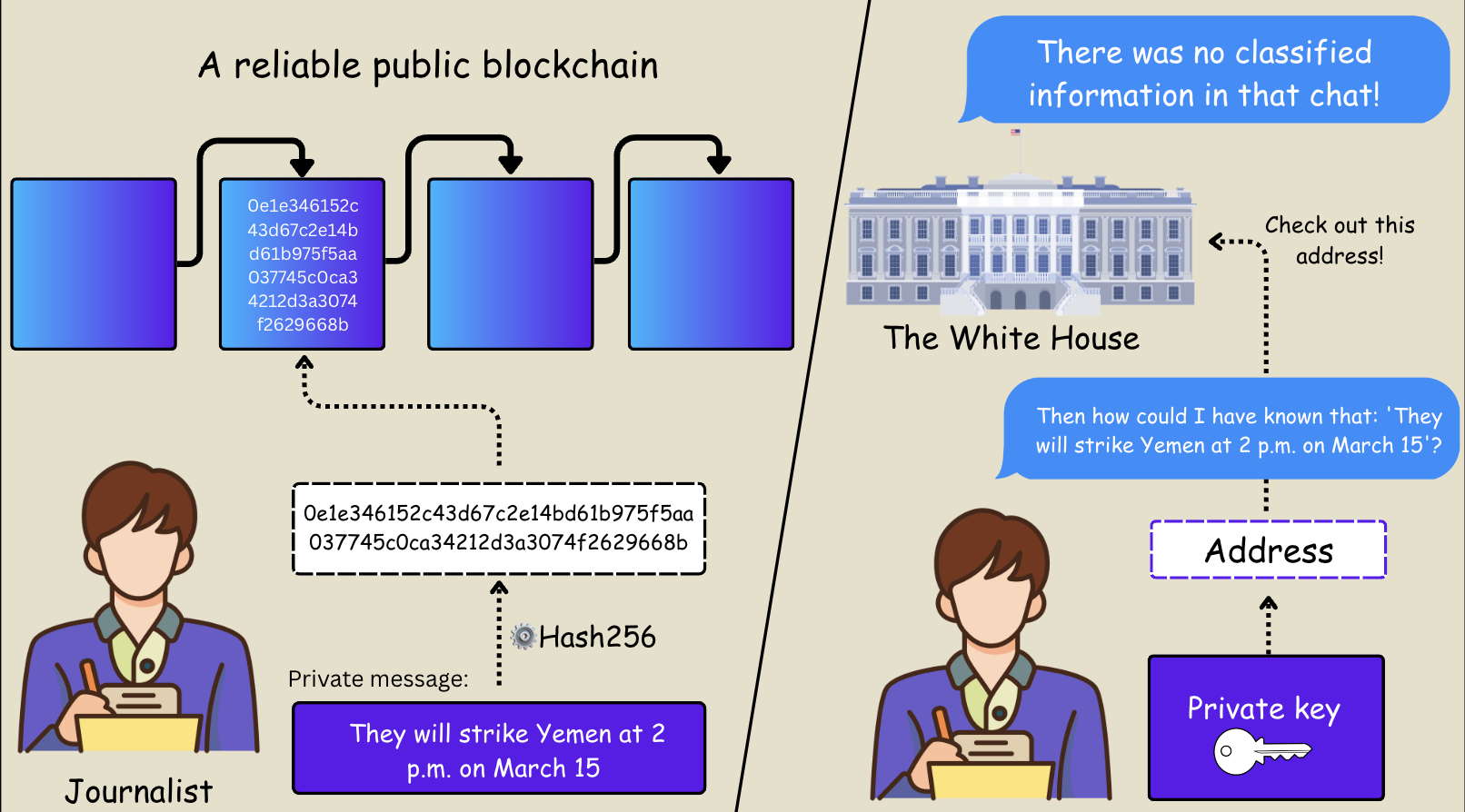
Course of diagram: Proof of existence utilizing blockchain | Supply: Courtesy of the creator
This course of creates an plain, timestamped file confirming {that a} particular unique message existed and was identified to the writer on the time the blockchain transaction was confirmed—all with out revealing the content material publicly till the journalist chooses to take action.
Learn extra: Past consensus: Transaction privateness is blockchain’s subsequent safety frontier | Opinion













